For millions of people, password management and online security is opaque and maddening. Websites with password requirements tell you they have to be a specific number of characters long, be upper and lower case, have numbers and sometimes even special characters - like $#%^1mpo55ibleToRemember! So many people have scribbled passwords in the backs of notebooks shoved into their desk drawer. In many instances, these books or pieces of paper include passwords to sensitive accounts like bank and .gov accounts. In others, the accounts are associated with social media and other public-facing accounts. In the event of an account breach or a fire, the loss of these passwords can lead to firing or even loss of control of online accounts that directly impact how one makes ones living.
Some sites, to reduce the pain of creating an account, may let you choose your own. Users then often choose a 'difficult' password they can remember and use that same password over and over.
The problem with this approach is that in the event of one account being breached by hackers, that password is in the wild. Datasets are sold on the dark web and hackers will often use as a point of departure previously-known passwords for a particular account for other accounts. This means that where an email address is known and is one of the login elements to identify a user, then all that needs to be breached is the password. If you are one of those people who uses the same password over and over, then breaching your account becomes much simpler. A password breach on that one password means hackers stand to win on all of your accounts.
Don't use an easy to guess password. Each year, security companies publish the most commonly used passwords, like 123456, qwerty, logmein, or Password1. The time it takes for a hacker running an automated script with these kinds of common, easy passwords can be as little as a few minutes. Don't use an easy to guess password. Each year, security companies publish the most commonly used passwords, like 123456, qwerty, logmein, or Password1. The time it takes for a hacker running an automated script with these kinds of common, easy passwords can be as little as a few minutes. For a laugh, visit the Wikipedia page on this and see whether you're using any of these 'worst' passwords. It's updated annually.
Other people save their passwords in their browsers. This is an improvement over a notebook in a drawer or re-using passwords, but still not ideal. It certainly offers the advantage of using complex non-repeating passwords. And browsers have stepped up their game regarding security. Chrome, the most popular browser will even sync your passwords across platforms - but the catch is you have to be logged into a Google account the entire time on all your hardware - phone, laptop, and tablet.
The EU privacy regulations - GDPR - that came into effect in May 2018 cast a spotlight on the pervasiveness of data and the degree to which big players monetize our data. For Google, you giving your passwords to them while logged into their proprietary browser provides them with unparalleled insight into your private life. All your browsing while logged in on all your hardware becomes their data. Admittedly, this is not strictly speaking a password management issue, but it does touch on the blurring of lines between online security, data ownership, and privacy. It also provides for a single point of failure, which is never a safe risk management practice.
If you like the idea of browser-based password management, consider instead using a different browser like Firefox when logging into accounts and conduct all your other personal and public business in a separate browser.
But if you've been hacked or have finally been persuaded to take your online security seriously, you're best served by turning off your browser password saving feature and using a password manager. A password manager is a utility that saves your passwords and will auto fill out your forms. It's a piece of software that runs completely separately from your browser and operating system and uses encryption to keep your passwords safe. The top password managers like Dashlane and LastPass will also tell you if there's been a breach online and flag any of your accounts that may have been compromised. They will run across different pieces of hardware, so you can use it on your phone, tablet and laptop and even on personal gear like your Apple watch. They will also flag whether you've used a password more than once and just how secure your password is. Both offer automatic, random, complex, password generators, so you don't have to try and think of a complicated jumble of numbers and letters each time you have to log into or create an account.
Good password managers like Dashlane or LastPass have free versions, but even their premium offerings are cheap at the price given the cost of even a single password breach. Don't wait till you've been hacked to make the change. Switching your passwords over to a password manager if you're on paper is tedious, but a good password manager will import passwords from your browser, making it simpler.
Lastly, put on your calendar and take the time each year to do a password and account audit. During that audit, change passwords in any account where you've repeated the same password somewhere else.
Also, during the audit, look at dormant accounts you've created. In many instances, we have to create an account to use a service or buy a product that we use only once, then forget we had it. Because not all companies practice good online security, should any one of those databases be hacked, your information is out in the wild. If you're not going to regularly use an account, consider closing or deleting those one-off accounts.
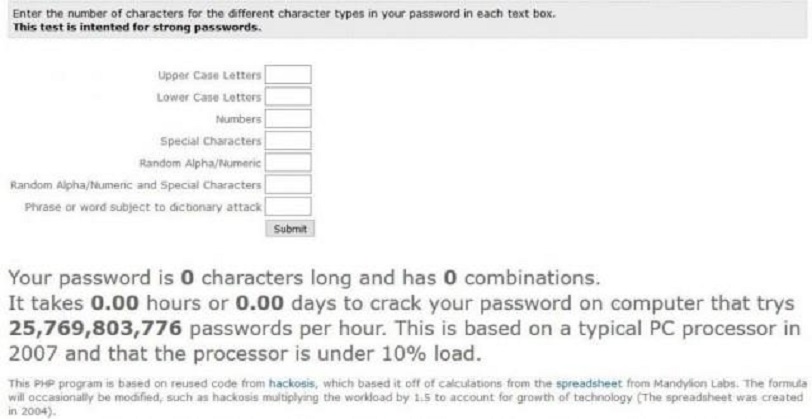
FOOTNOTE - the header image to this piece is from an online calculator at Tulane University that will check how long it will take to brute force crack a password.



Subscribe