In a 48-hour period, I received a series of Friend requests on Facebook, all from people I didn't know or with whom I hadn't done business. The requests were out of sync with my marketing, and statistically were unlikely. This blog looks at ways to protect yourself from requests to connect from fake accounts.
My first thought was that in the run-up to the U.S. elections, this was probably part of parties and candidates building up fake account portfolios to be able to bolster support for positions by using these bots as a kind of greek chorus. These are the accounts that shout the talking points and jump on naysayers. If you have enough of them, their point of view becomes overwhelming.
But these are not the only source of fake accounts. Fake and malicious connections on social media are used to put together pieces of data needed for ID theft and other scams.
Fake profiles on social media are hardly new. Which Twitter account owner hasn't been followed by an account offering 5,000 followers for only $15? It also pays to search for your own social media accounts from time to time to check against impersonation. This is a quick way to duplicate an authentic-looking account that can then be used nefariously or as one of those '5,000 followers for only $15'.
So when you get a friend request on Facebook from someone you don't know, or on Linked In, a request to connect, do your homework before simply accepting. My approach includes the following:
- I contact them before accepting and ask them why they want to connect. What's their interest? Have they read anything on my timeline?
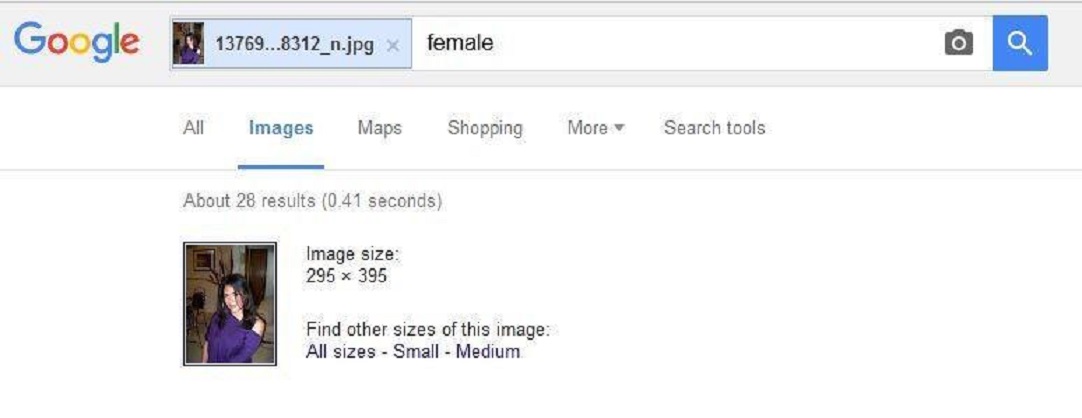
- I reverse search their profile pictures. Often fake accounts will show up quickly in a Google reverse image search.
- I read their profile information. If it doesn't add up, I decline.
If they don't get back to me, I decline. On Linked In, if they don't respond to my follow-up email about doing business, I disconnect. If I come across a fake account, I report it.
 In today's batch on Facebook, I got a friend request from a soldier in Miami, Oklahoma. His image didn't reveal anything on Google, except that the name on his tunic was Carpenter and his account was Capenter. So I messaged. He said he was interested in doing some business, so I was prepared to talk further. In a matter of three sentences, it was clear he was African - I'm African, I can tell - and not a white guy from Mi-amah which is how the good ol Okies from that town say it. My wife was from there and I've lived in Oklahoma. So, bye-bye. Decline, block and report to Facebook.
In today's batch on Facebook, I got a friend request from a soldier in Miami, Oklahoma. His image didn't reveal anything on Google, except that the name on his tunic was Carpenter and his account was Capenter. So I messaged. He said he was interested in doing some business, so I was prepared to talk further. In a matter of three sentences, it was clear he was African - I'm African, I can tell - and not a white guy from Mi-amah which is how the good ol Okies from that town say it. My wife was from there and I've lived in Oklahoma. So, bye-bye. Decline, block and report to Facebook.
The picture of the soldier to the left is the one that was appropriated by the scammer. The scammer couldn't spell 'Carpenter'.
The second request, Facebook beat me to it. They closed his/her account before she responded to my message. The fake account was using a picture of a female sergeant in the British army.
 A third was a Chinese account that had suddenly gone Caucasian. It required a little scrolling down their timeline, but there it was.
A third was a Chinese account that had suddenly gone Caucasian. It required a little scrolling down their timeline, but there it was.
A common scam from Asia, but not only that part of the world is to target widows and widowers, who suddenly find themselves popular. They get befriended, and not long into the 'friendship' their friend's mother becomes ill and needs dollars for the treatment. For someone emotionally fragile, this kind of scam is successful too often.
The fourth, my Google reverse image search revealed a string of links about frauds. Not even subtle, that one. A common feature to fake accounts is they have very little information on their profiles about who they are, where they work and who their friends are. Often, an image search will quickly either verify who the person is or isn't. People who aren't hiding stuff about themselves usually post material that is both banal and in its banality, authentic. Their dogs or cats, their garden, their workplace, traffic jams, other identifiers. They will often have only one or two posts in an entire year and very little that's easily verified.
The fifth, I'm still waiting for a response. The request was from someone who had a woman's picture as their profile picture, but their gender was male. If nothing is forthcoming in 24 hours, he/she will be declined.
For people who have very active social media accounts, being this attentive to accepting requests to connect may be difficult. For Coherent Marketing accounts - and my personal account - I take stewardship of my connections to people I know and have worked with seriously. My contacts are relationships and many of the people on my friends list or contacts are people I have worked with as a journalist or served as a client. Except, perhaps on Twitter, which is a different kind of social medium and requires an approach appropriate to its style.
So next time you get a request from someone you've never met, find out why they want to connect, first. They may not be who they appear to be. And if you have questions about how to more securely manage your social media accounts or whether the followers you have are real or fake, CONTACT US.



Subscribe