Two-factor authentication is a method of enhancing the security of web logins to your site. It separates a website login with another form of identification that a user has such as an email address or better, a mobile phone, which will presumably be in the user's possession. If you have a website that uses it for customer-facing applications, make sure that your process is capable of managing authentication at peak times.
An example of poor management of this process is Nationwide Insurance, with whom I have personal experience. In the course of the past few months, Nationwide Insurance has twice had failures with its authentication. This type of failure drives frustration levels up among customers because it is time wasting and that is unnecessary. Moreover, it occurs at a time when people are parting with cash. While they are waiting - in my instance more than half an hour for two failed login attempts plus a phone call - customers are tempted to search for a competitor who wants their business. Requiring a phone call is standard, because it enables the provider to validate the account.
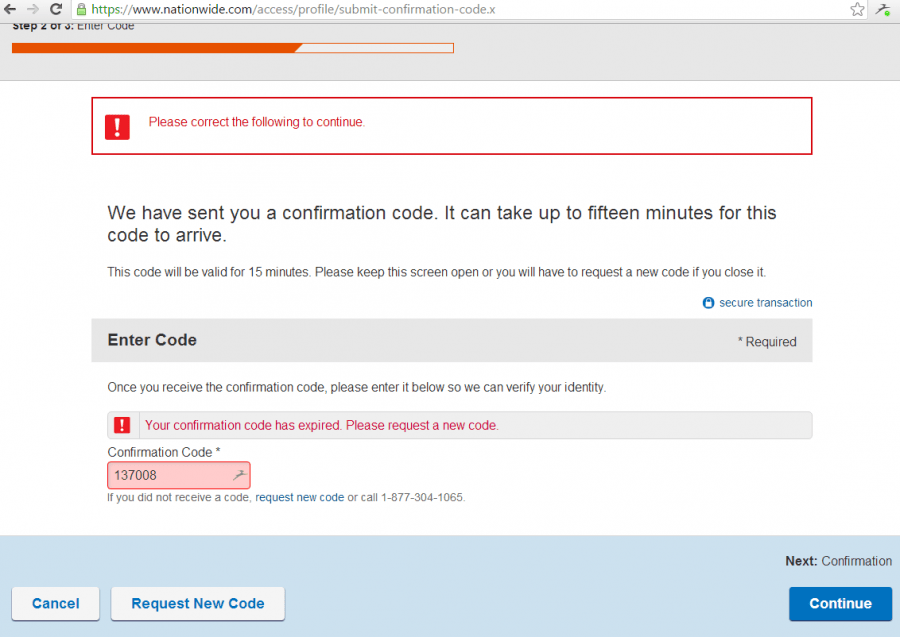 If a phone call is needed, make sure staff are well-trained and have in place a way to mitigate frustration - something Nationwide does not practice. Having customers wait on extended hold times while trying to make what should be a quick payment is rubbing salt into the wound, especially when the customer has been compliant.
If a phone call is needed, make sure staff are well-trained and have in place a way to mitigate frustration - something Nationwide does not practice. Having customers wait on extended hold times while trying to make what should be a quick payment is rubbing salt into the wound, especially when the customer has been compliant.
Usuallly, these types of issues are systemic, so it doesn't affect just one person. Small numbers can be shrugged off, but remember the public relations cost to companies like Comcast for their 'impossible to leave' customer service or Netflix for their price change. Multiply this kind of irritation across an affected customer base on social media and it can rapidly turn into a dip in quarterly profits. Moreover, if the missed payment deadline leads to penalties on bills and is a persistent fault, it is grounds for a class-action suit.
The simple fix is to ensure that the two-factor authentication process has enough bandwidth - plus a safety margin - to cope with peak traffic like at the end of a month or during annual registration periods and avoid PR fallout to the brand and social media staff having to put out fires.



Subscribe