As we embark on a journey into the realm of content management systems, one name stands out prominently: Joomla. In this article, we delve into the roots of Joomla, its etymology, and its significance in the digital landscape.
Let's commence our exploration with the name itself. While Joomla may seem like a coined term to some, its origins trace back to the Swahili language, particularly the word "jumla," meaning "all" or "as a whole." This linguistic connection not only adds depth to Joomla's identity but also reflects its inclusive nature, catering to diverse communities across the globe.
 No comments
No comments- Details
- Written by: Mohamed Abdelaziz
- Category: Learning
- Published:
- Hits: 2835
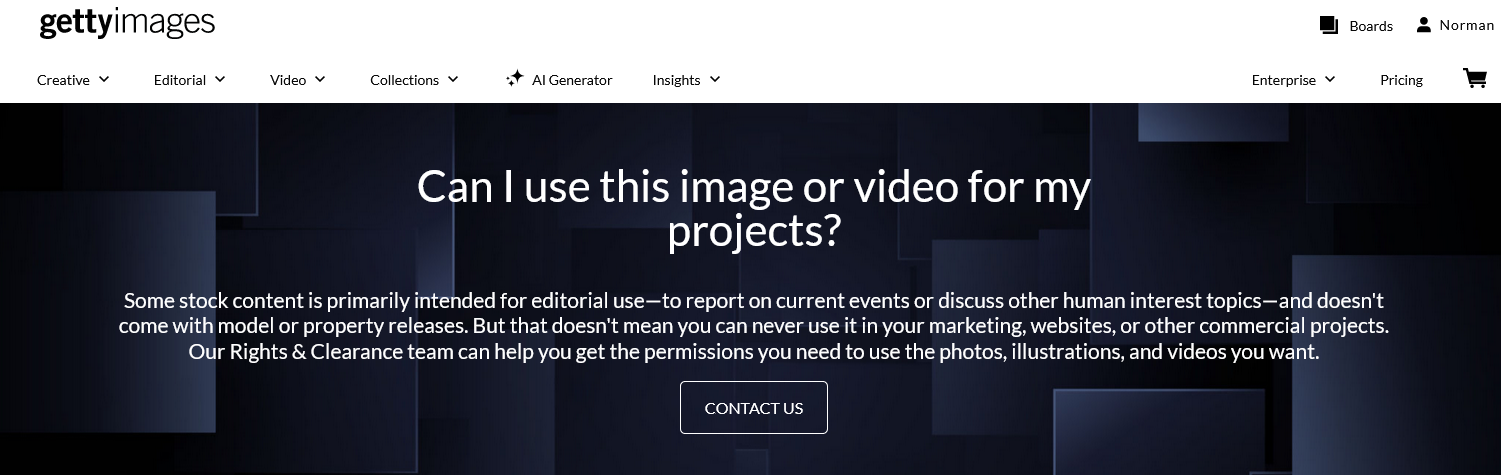
Fresh content on a website is one of the most important ways search engines rank where you will be found - on page one, or buried.
Content marketing uses online content to increase the visibility of an organization and is an effective marketing method. Done right, it can help you get to page one.
Many organizations have experienced staff, provide good services, and have everything needed to create great content with the regularity needed for this kind of marketing, but find it difficult to do so. We can solve that for you. We will turn what it is you do into effective web content. In short, we make content marketing easy for you. Contact us to find out about our rates and to discuss how we can help.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 10223
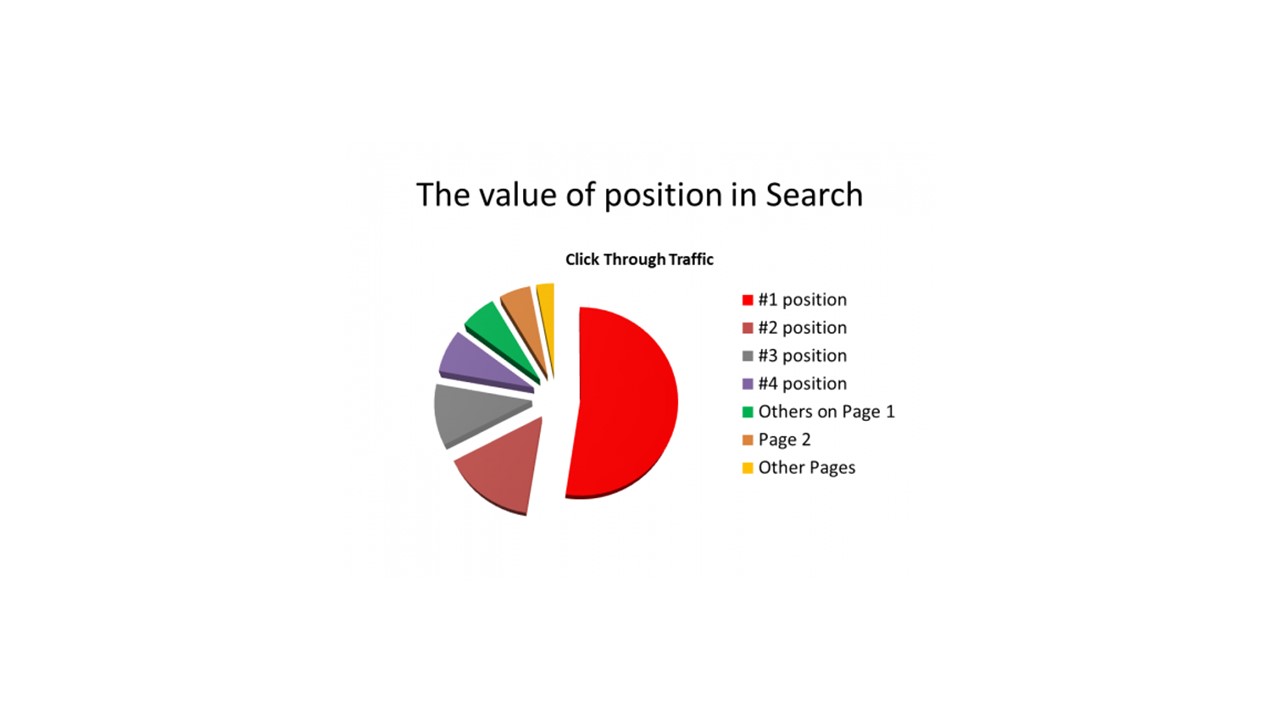
Companies relying on their websites for strategic positioning, content marketing, and sales should monitor their Google Search Console regularly. This may seem obvious, but for many small businesses where owners wear many hats, taking the time to do so can seem like a low priority. We advise our small business clients to do so monthly, more often if they are running any online marketing campaigns. On behalf of one of our clients, we recently received a Google email saying: "New AMP issue detected for site..."
AMP is short for Accelerated Mobile Pages Project, which is an open source initiative. For a variety of reasons relating to its business model, Google is heavily invested in the mobile web, so when you receive an email like this, pay attention, as it is negatively impacting your website's search results. In this particular email, the reason given was: Custom JavaScript is not allowed. Integrated Media Strategies builds only open source sites and uses vendors who produce well-coded commercial open-source licensed extensions, so it seemed odd that something had changed, prompting the email.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 3754
For millions of people, password management and online security is opaque and maddening. Websites with password requirements tell you they have to be a specific number of characters long, be upper and lower case, have numbers and sometimes even special characters - like $#%^1mpo55ibleToRemember! So many people have scribbled passwords in the backs of notebooks shoved into their desk drawer. In many instances, these books or pieces of paper include passwords to sensitive accounts like bank and .gov accounts. In others, the accounts are associated with social media and other public-facing accounts. In the event of an account breach or a fire, the loss of these passwords can lead to firing or even loss of control of online accounts that directly impact how one makes ones living.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 1424

Coherent Marketing has worked with SCORE Raleigh for the past several years to help small businesses improve their online security. In an increasingly-connected world, small businesses are vulnerable to a range of malicious attacks. And because of this connectedness, an intrusion in one area can translate into a much broader problem. A successful malicious attack can be terminal to a small business.
Our online seminar is a cost-effective way to learn the basics that a small business needs to avoid a costly hack or ransomware.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 3817

In 2016, the CEO of Coherent Marketing, Norman Smit, was invited by the Raleigh office of the SCORE small business mentoring organization to offer a series of seminars in the first quarter of 2017. The seminars, which will take place at libraries across Wake County has been titled "The Smartphone-Wielding Small Business Guide to Content Marketing".
GET THE SEMINAR SLIDES HERE.
The ground we cover includes:
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 4837
- Reputation ransomware - beware business 'directories'
- Hacks and your relationship with passwords
- SEO Snake Oil
- Simple steps to protect yourself against fake social media connections
- Memes skewer PR & branding #Fails
- Taking the PR pain out of two-factor authentication failures
- Twitter Impersonator
- Insider speak made easy - explaining those abbreviations and acronyms
- Starting social media at your organization
- Making video work for content marketing