In 2016, the CEO of Coherent Marketing, Norman Smit, was invited by the Raleigh office of the SCORE small business mentoring organization to offer a series of seminars in the first quarter of 2017. The seminars, which will take place at libraries across Wake County has been titled "The Smartphone-Wielding Small Business Guide to Content Marketing".
GET THE SEMINAR SLIDES HERE.
The ground we cover includes:
 No comments
No comments- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 0 4246

In an internet age, regular reviews of your company's digital footprint and how it may have been appropriated by bots scraping your content is important to do on a regular basis. Sites seeking to mash ransomware with customer reviews are now popping up. The way it works is your information is scraped from your site or social media pages and then a page created for your company. Reviewers can then post whatever they choose about your company. You are required to log into the site and 'claim' your listing. In some instances, you may be charged to transform your 'free' listing into some kind of service-based listing - for example, premium accounts have the additional options they can take when a negative review is posted. In many instances, the identities of the reviewers are obscured so that it is impossible to tell whether the reviewer is a real person or not, or an employee of the review site. An additional danger is the site may be actively soliciting you to claim the listing with incorrect information and requiring additional information with the goal of data mining, identity theft or levying charges to your bank account. Treat sites like these in the same way as you would treat spoofed emails from legitimate accounts you own such as your bank account and do not give them your information.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 0 1362

Yahoo was hacked in 2014. Shamefully, the news was released only in September 2016. It was one of the biggest data breaches in history and even encrypted passwords were stolen. So, firstly, if you have a Yahoo account, change your Yahoo password now.
But the breach may impact you beyond just your Yahoo account. When Integrated Media Strategies builds websites for clients or helps them with their small business email accounts, we create long, randomized passwords like s0cnZS)XD'H[4RmkL. We'll get grumbling that they are impossible to remember. We usually spell out the cost of a site brought down by malware or that's been hacked because of poor security practices. "Username: Admin Password: Admin" is something we've seen too often. Clients will also entrust us with access to their hosting and other accounts, and when we see their passwords, it's often a variant of their children, dog or something like "Passw0rd". They reuse that same password everywhere to save the hassle of remembering multiple passwords, unaware of how a breach in one place can have a cascading impact on all their accounts.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 0 1328

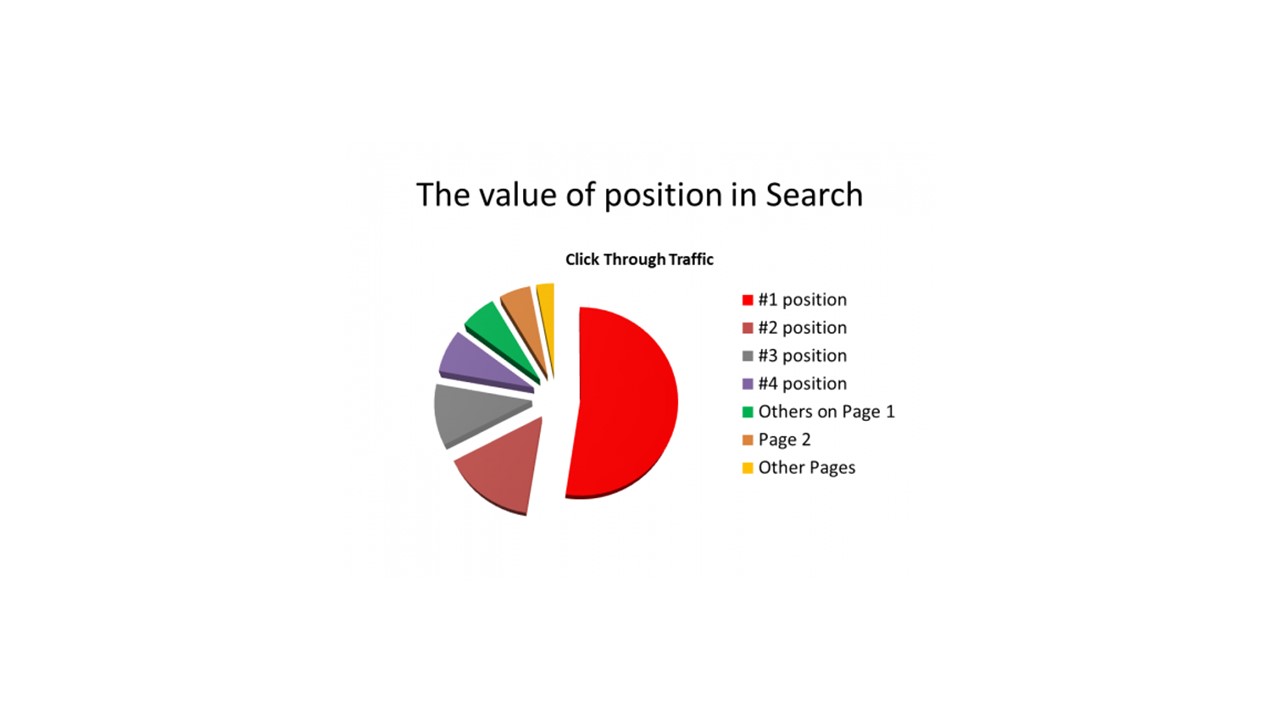
One area of the work we do is helping small and micro businesses as a digital communications service provider and coach. Having been involved in more than a dozen startups over my career, I know that money and resources are usually tight at startups. So nothing irks me more than getting the type of call I did recently from a client saying they were going to work with a 'SEO specialist' who had told them the web platform their site was built on was unsuitable for SEO, which stands for Search Engine Optimization, and that it needed to be redone and then they could get them page one rankings in a week.
The platform on which their site was built is a leading open-source solution well-suited to the application for which it was built. For small business owners, if it sounds too good to be true, it probably is.
So let's look at the changing landscape of SEO and whether a technical solution will produce the results promised.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 0 1493
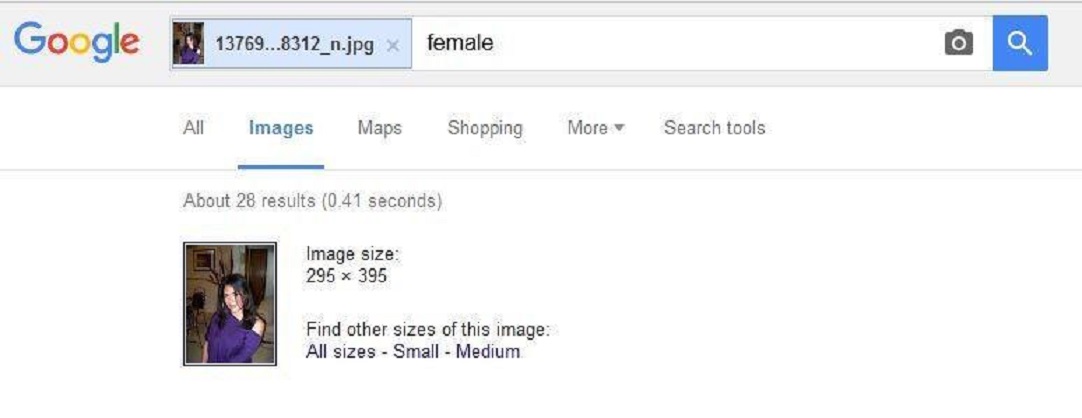
In a 48-hour period, I received a series of Friend requests on Facebook, all from people I didn't know or with whom I hadn't done business. The requests were out of sync with my marketing, and statistically were unlikely. This blog looks at ways to protect yourself from requests to connect from fake accounts.
My first thought was that in the run-up to the U.S. elections, this was probably part of parties and candidates building up fake account portfolios to be able to bolster support for positions by using these bots as a kind of greek chorus. These are the accounts that shout the talking points and jump on naysayers. If you have enough of them, their point of view becomes overwhelming.
But these are not the only source of fake accounts. Fake and malicious connections on social media are used to put together pieces of data needed for ID theft and other scams.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 0 1520

I live and work in the state of North Carolina, which this year saw it's Republican-dominated legislature call a special session and enact what has become known as the Bathroom Bill. It was initiated and signed into law in a single day. It is a misguided piece of legislation that strips a number of well-established workplace rights from citizens, along with the clauses pertaining to transgender people and bathrooms. From a marketing communications and positioning perspective, it has been an unmitigated disaster for the state, and it has garnered a lot of ironic humor skewering the people and issues the bill supposedly addresses in the form of memes.
Despite the protestations of Governor McCrory to the contrary, the negative fallout was quick and brutal, and the ongoing impact is continuing. Estimates have put the loss of revenue at $5 billion annually from industry and business pullouts, boycotts, and withdrawal of Title IX federal dollars. Other estimates put the cost to the state at 20% of its annual budget. This goes hand in hand with changing the perceptions of the state from moderate to a conservative backwater. This directly negatively impacts its ability to tap into the progressive, forward-looking and innovative thinking required by entrepreneurs and and modern companies seeking employees with competitive skills-sets in a disruptive, 21st Century economy.
While comments sections generate more heat than light, especially in a year in which Donald Trump has made racism and intolerance mainstream again, the growth of a plethora of memes ridiculing the legislation and regressive policies deserves some consideration from a marketing communications and positioning perspective.
- Details
- Written by: Norman Smit
- Category: Learning
- Published:
- Hits: 0 1433
- Taking the PR pain out of two-factor authentication failures
- Twitter Impersonator
- Insider speak made easy - explaining those abbreviations and acronyms
- Starting social media at your organization
- Making video work for content marketing
- The skydivers guide to communications risk management
- Doing content marketing cost effectively
- New media - implications for management structures
- Number #2 on Google
- Joomla Help - how to create a link in text